DIDKit v0.2.1 Now Available on Cargo
This week, we’re proud to announce the v0.2.1 release of DIDKit on Cargo, and DIDKit-WASM v0.1.7 on npm.

This week, we’re proud to announce the v0.2.1 release of DIDKit on Cargo, and DIDKit-WASM v0.1.7 on npm.
DIDKit is a cross-platform toolkit for working with W3C Verifiable Credentials and Decentralized Identifiers. It has SDKs in JavaScript, Java, Python, and more, and it even runs in the browser frontend. It supports a variety of cryptographic algorithms allowing it to seamlessly bridge trust across different blockchains and public key infrastructures, including traditional X.509 and TLS.
We wrote DIDKit in Rust due to its memory safety, expressive type system, and suitability across a variety of systems and environments. For example, the Rust ecosystem has already explored WASM compilation targets in support of single-page apps running in browsers, and we wanted to be able to support those and also browser extensions with DID and VC operations.
To try out DIDKit using the command line from a Rust-enabled environment, simply run the following:
$ cargo install didkit-cli
$ didkit --versiondidkit-cli 0.1.0
$ didkit generate-ed25519-key | tree key.jwk
{"kty":"OKP","crv":"Ed25519","x":"g2rSWdI1YGbOTwkzQl2HbqZ-LJNS69p-GZdNdv6N7OU","d":"1mZOfhcQa3JG_P-jqyyAdVSaSluh9p1BwP0GATOtECI"}
$ didkit key-to-did key --key-path key.jwk
did:key:z6MkoJFvkSmF2bjqGbu3fBj71hTRmj9ScwVFoA99JGW2iTnt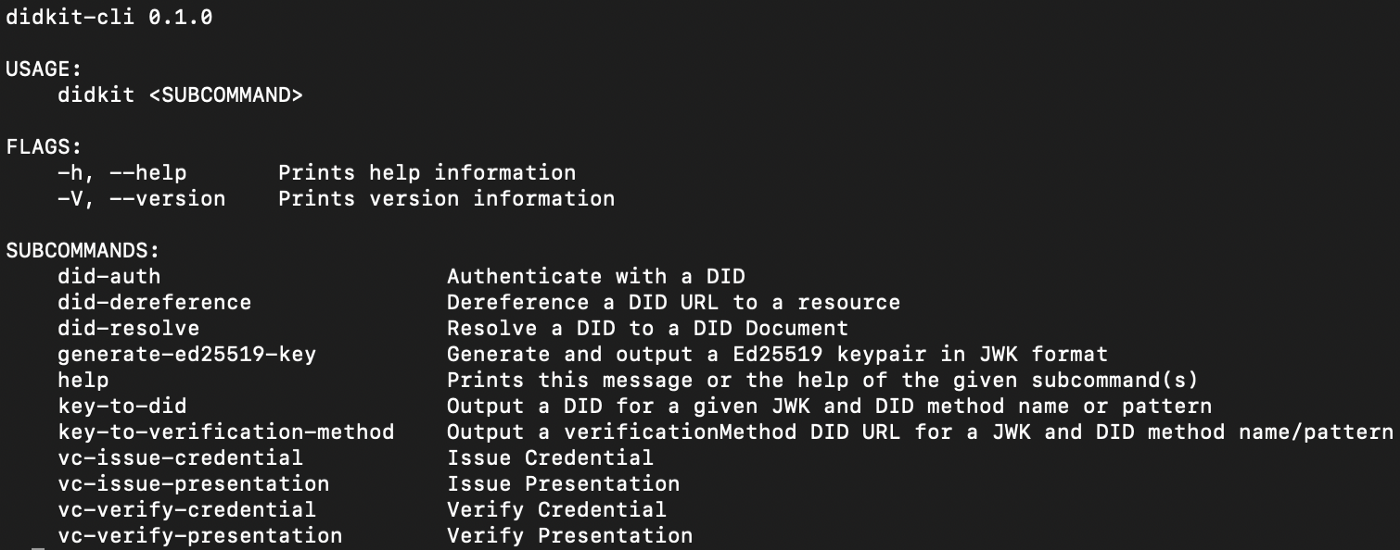
Once you have DIDKit installed, you can run an example script here that will show you how you can issue, present, and verify a credential. For more details, please see our documentation here.
Follow us on Twitter
Follow us on LinkedIn