Single-Player Ready Apps
The Single-Player Ready (SPR) app architecture allows users to maintain control over their data while also participating in a larger network of related content. It has applications including even sensitive information that should first and foremost be under the user's control.

When you reflect on your most used apps, platforms, and services, you’ll notice how often you're the creator.
You create your profile on LinkedIn, recommend restaurants on Yelp, post thoughts on Reddit, share your life on Twitter or Instagram, and design your latest app in Figma, to name a few. You typically upload your data to the platform, which provides distribution across its vast network along with free hosting and slick user interfaces. In return, it expects to make money from your content and attention.
At SpruceID, we think that the content you make should, in fact, belong to you. A platform with its own (sometimes competing) interests shouldn't be able to lock your content to its databases or disable your entire account on a whim. Some platforms provide data exports, but almost always as archive files lacking in data portability. This form of lock-in reduces your autonomy and stifles innovation. You should be able to do what you want with your data.
We could start with portable data formats that declare you as the owner when you create original content. This content can be stored in your own private instances of these apps that you control, and you can give out additional access how you see fit. For example, you could maintain private lists of book reviews, and choose which lists you'd like to share to a friend, without an intermediary that could remove your (or your friend's) access to those lists. They are useful in their own right, without a platform. As a result, instead of you signing in to the platforms with fiefdoms over your data, the platforms could sign in to your data vault that you control entirely.
We also recognize that digital platforms are incredibly powerful distribution networks serving content creators for cheap or free, and this is especially important for small creators and new brands. However, it is you who owns the content and it should be your explicit choice on which platform to post, and on what terms.
The Single-Player Ready (SPR) app architecture allows users to maintain control over their data while also participating in a larger network of related content. It has applications beyond just book or restaurant reviews – medical histories, financial records, or any other sensitive information that should first and foremost be under the user's control.
This next generation of consumer apps is enabled by the proliferation of user-generated content, widespread user adoption of smart devices with digital signing capabilities, and the increasing affordability of cloud computing for individuals. These technology shifts have made it feasible for users to directly manage (or delegate management of) their data instead of relying on de facto management by a few large platforms, separating the custodianship of the data versus use across networks. Digital signing further allows users to originate content with authenticity that can be verified, and create data licenses or digital permission slips that automate compliance with data privacy rules.
The architecture of users bringing their own data has been pioneered by protocols such as Sign-In with Ethereum, ActivityPub, Secure Scuttlebutt, and Solid. To date, these have faced adoption hurdles due to user experience difficulties caused by the usage of digital keys, the need to perform server setup, and complex interfaces for user-granted permissions. With Single-Player Ready apps, these hurdles can be overcome because applications can now offer unparalleled user experiences while maintaining user control and privacy.
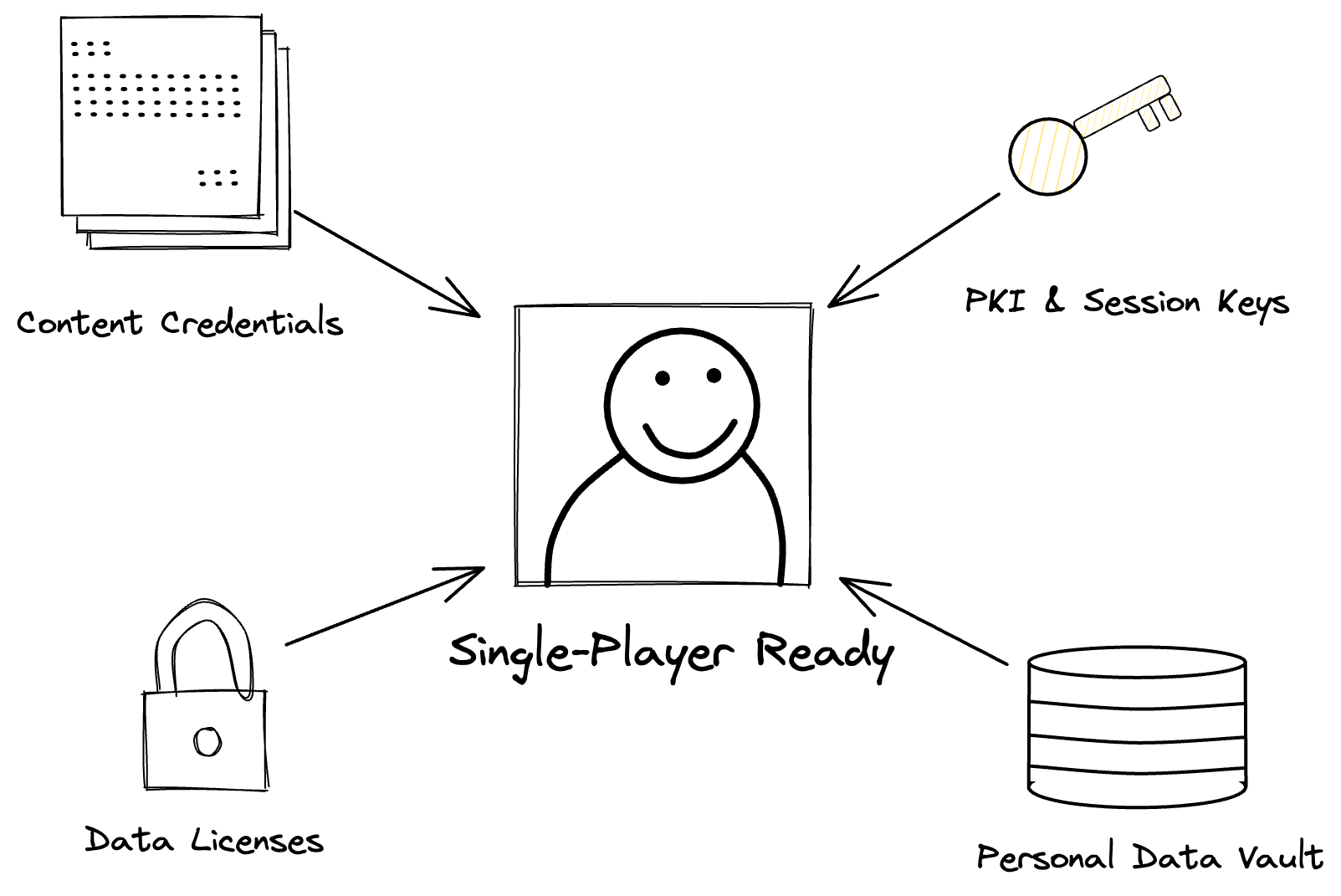
The Building Blocks of Single-Player Apps:
- Key Management: Users can create digital signatures and use encryption over their data. This allows users to originate authentic content, authenticate themselves, grant access to their data vaults, or delegate power to other keys controlled by them or someone else. Users should have many keys, and not concentrate all their control into one that can be lost or stolen. Instead, this should match expectations in the physical world using advances in public key infrastructure (PKI).
- Content Authenticity: Users can create digital signatures over metadata that corresponds to original content, such as tweets, posts, follows, messages, videos, images, reviews, and more. This allows users to establish provenance for their content, especially when attested with other signatures from witnesses such as other users, platforms, or blockchains. This creates content authenticity certificates that can be verified.
- Data Licenses: Users can issue and revoke data licenses that describe the policies for how their data must be accessed and handled, providing more control over how their information is shared and used, and by whom.
- Personal Data Vaults: Users can securely store and manage their digital information, including content. Access to the content within these vaults is granted via digitally signed permission slips (known as capabilities), which can be revoked later.
These core building blocks introduce authenticity and integrity into digital interactions with Single-Player Ready apps. Today, the root of data provenance is typically in a cluster of platform-hosted SQL databases, but there's no reason why data provenance can't be rooted in digitally signed content that users independently hold. The transition away from centralized data silos will allow users to have fuller control over their digital interactions.
The Building Blocks: Keys are Digital Empowerment
One of the critical components in this new paradigm is the concept that "keys equal digital empowerment." Traditionally, users have relied on either frequently-lost passwords or "Big Login" providers, such as Facebook, Google, or other similar services, to manage their online identities and data. However, with the advent of key-based authentication standards like Sign-in with Ethereum or passkeys, users can sign messages digitally to directly authenticate themselves and may be able to further authorize access to their data.

However, today's UX for signing different types of transactions or performing encryption does not always reflect the smooth, frictionless interactions we are used to in most consumer applications. If every time a user wanted to “like” a tweet or “follow” someone on Single-Player Ready Twitter, they were faced with a cumbersome digital signing dialog and more confirmations to persist their content, they probably wouldn't be users for long.
This can be solved by allowing users to use different keys for different purposes. For example, some keys might be generated on the spot (session keys) to perform certain pre-authorized actions without a slew of confirmation dialogs. Other keys might be long-lived, able to grant permissions to the session key after a confirmation dialog. We can innovate on signing standards and better key management to reduce friction for users while also maintaining integrity.
Keys with existing privileges can manage access to resources by delegating some (or all) of those privileges to another key. For example, you may want to give your new physician's office access to your medical history since 2015. In this scenario, you, the owner of your medical data, create a data license that entitles the physician's office to retain your general medical history since 2015 for 5 years, or until you revoke the license.
To retrieve the actual data and associated data license, you grant a permission slip to the physician's office so they can access your data vault over the next hour for those specific files, and nothing more. On future visits, you may decide to adjust the data license so the physician's office can further share your data with certain medical specialists, but no further. This kind of system operates on the principle of least privilege, where an entity is granted the minimum resources and authorizations to perform a specific function and nothing else.
You can use these permission slips (often known as "capabilities") to grant others access to your digital resources, and you can also revoke that access at a later time. Enter user-controlled data vaults (or "personal clouds"), which respect the rules set in these permission slips. At SpruceID, we believe that a user should also be able to define where their data live by authorizing who can host the infrastructure for their data. As standards for these permission slips (e.g., JWTs, UCANs, and ZCAPs) gain adoption, they will be accepted in more and more places.
From Single Player to Multiplayer
While "Single-Player Ready" applications can be useful (and fun) without anyone else, they are much more powerful when upgraded to "multiplayer" applications, where interaction with others and network effects become very important.
We can think about how a Single-Player Ready Yelp evolves to be multiplayer. You would begin with your own personal version of Yelp. You can write the most scathing reviews about your experience at your most recent dinner if you want. Your reviews are stored in your personal data vault–your personal space to store all your honest thoughts, where you control access to the information rather than a centralized application.
From there, you can grant permission slips via digital signing to share select reviews with other "Personal Yelp" instances based on their digital accounts, such as Ethereum addresses, decentralized identifiers, or even email addresses. You can also grant data licenses that allow further sharing to your friends’ friends, which can be used to crowdsource reviews from a trusted circle. If one of those friends or friends’ friends leaves a review you vehemently disagree with or find offensive, you can eject them from your own review system. Because their content is rooted in their digital keys, you can filter out all of their reviews with a single setting - across all other places where they use those keys. You could message them using end-to-end encrypted messaging to deliver the sad news they have been removed from your reviews circle of trust, assuming they haven't blocked you first.
Single-Player Ready apps have the potential to revolutionize how we interact with online applications and services. They empower users with data portability, freedom from digital lock-in, and minimized control from intermediaries. They also enable impressive user experiences that can delight while maintaining security. The future of digital identity and data ownership is in our hands, and it’s time to take control.
About SpruceID: SpruceID is building a future where users control their identity and data across all digital interactions. If you're curious about integrating SpruceID's open-source libraries into your project, chat with us in Discord or check out our libraries on GitHub.





